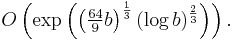Integer factorization
In number theory, integer factorization or prime factorization is the breaking down of a composite number into smaller non-trivial divisors, which when multiplied together equal the original integer.
When the numbers are very large, no efficient integer factorization algorithm is publicly known; an effort concluded in 2009 by several researchers factored a 232-digit number (RSA-768) utilizing hundreds of machines over a span of 2 years.[1] The presumed difficulty of this problem is at the heart of certain algorithms in cryptography such as RSA. Many areas of mathematics and computer science have been brought to bear on the problem, including elliptic curves, algebraic number theory, and quantum computing.
Not all numbers of a given length are equally hard to factor. The hardest instances of these problems (for currently known techniques) are semiprimes, the product of two prime numbers. When they are both large, randomly chosen, and about the same size (but not too close), even the fastest prime factorization algorithms on the fastest computers can take enough time to make the search impractical.
Many cryptographic protocols are based on the difficulty of factoring large composite integers or a related problem, the RSA problem. An algorithm which efficiently factors an arbitrary integer would render RSA-based public-key cryptography insecure.
Contents |
Prime decomposition
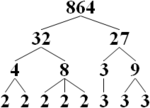

By the fundamental theorem of arithmetic, every positive integer has a unique prime factorization. (A special case for 1 is not needed using an appropriate notion of the empty product.) However, the fundamental theorem of arithmetic gives no insight into how to obtain an integer's prime factorization; it only guarantees its existence.
Given an algorithm for integer factorization, one can factor any integer down to its constituent prime factors by repeated application of this algorithm.
Current state of the art
A team at the German Federal Agency for Information Technology Security (BSI) holds the record for factorization of semiprimes in the series proposed by the RSA Factoring Challenge sponsored by RSA Security. On May 9, 2005, this team announced factorization of RSA-200, a 663-bit number (200 decimal digits), using the general number field sieve.
The same team later announced factorization of RSA-640, a smaller, 640-bit number (193 decimal digits), on November 4, 2005.
Both factorizations required several months of computer time using the combined power of 80 AMD Opteron CPUs.
In January 2010, the factorization of RSA-768 was announced.[2]
Difficulty and complexity
If a large, b-bit number is the product of two primes that are roughly the same size, then no algorithm has been published that can factor in polynomial time, i.e., that can factor it in time O(bk) for some constant k. There are published algorithms that are faster than O((1+ε)b) for all positive ε, i.e., sub-exponential.
The best published asymptotic running time is for the general number field sieve (GNFS) algorithm, which, for a b-bit number n, is:
For an ordinary computer, GNFS is the best published algorithm for large n (more than about 100 digits). For a quantum computer, however, Peter Shor discovered an algorithm in 1994 that solves it in polynomial time. This will have significant implications for cryptography if a large quantum computer is ever built. Shor's algorithm takes only O(b3) time and O(b) space on b-bit number inputs. In 2001, the first 7-qubit quantum computer became the first to run Shor's algorithm. It factored the number 15.[3]
When discussing what complexity classes the integer factorization problem falls into, it's necessary to distinguish two slightly different versions of the problem:
- The function problem version: given an integer N, find an integer d with 1 < d < N that divides N (or conclude that N is prime). This problem is trivially in FNP and it's not known whether it lies in FP or not. This is the version solved by most practical implementations.
- The decision problem version: given an integer N and an integer M with 1 ≤ M ≤ N, does N have a factor d with 1 < d < M? This version is useful because most well-studied complexity classes are defined as classes of decision problems, not function problems. This is a natural decision version of the problem, analogous to those frequently used for optimization problems, because it can be combined with binary search to solve the function problem version in a logarithmic number of queries.
It is not known exactly which complexity classes contain the decision version of the integer factorization problem. It is known to be in both NP and co-NP. This is because both YES and NO answers can be trivially verified given the prime factors (we can verify their primality using the AKS primality test, and that their product is N by multiplication). In fact, providing we require the factors to be listed in order, the fundamental theorem of arithmetic will guarantee that there is only one possible string that will be accepted; this shows that the problem is in both UP and co-UP.[4] It is known to be in BQP because of Shor's algorithm. It is suspected to be outside of all three of the complexity classes P, NP-complete, and co-NP-complete. If it could be proved that it is in either NP-Complete or co-NP-Complete, that would imply NP = co-NP. That would be a very surprising result, and therefore integer factorization is widely suspected to be outside both of those classes. Many people have tried to find classical polynomial-time algorithms for it and failed, and therefore it is widely suspected to be outside P.
In contrast, the decision problem "is N a composite number?" (or equivalently: "is N a prime number?") appears to be much easier than the problem of actually finding the factors of N. Specifically, the former can be solved in polynomial time (in the number n of digits of N) with the AKS primality test. In addition, there are a number of probabilistic algorithms that can test primality very quickly in practice if one is willing to accept the small possibility of error. The ease of primality testing is a crucial part of the RSA algorithm, as it is necessary to find large prime numbers to start with.
Factoring algorithms
Special-purpose
A special-purpose factoring algorithm's running time depends on the properties of the number to be factored or on one its unknown factors: size, special form, etc. Exactly what the running time depends on varies between algorithms. For example, trial division is considered special purpose because the running time is roughly proportional to the size of the smallest factor.
- Trial division
- Wheel factorization
- Pollard's rho algorithm
- Algebraic-group factorisation algorithms amongst which are Pollard's p − 1 algorithm, Williams' p + 1 algorithm and Lenstra elliptic curve factorization
- Fermat's factorization method
- Euler's factorization method
- Special number field sieve
General-purpose
A general-purpose factoring algorithm's running time depends solely on the size of the integer to be factored. This is the type of algorithm used to factor RSA numbers. Most general-purpose factoring algorithms are based on the congruence of squares method.
- Dixon's algorithm
- Continued fraction factorization (CFRAC)
- Quadratic sieve
- General number field sieve
- Shanks' square forms factorization (SQUFOF)
Other notable algorithms
Notes
- ↑ Factorization of a 768-bit RSA modulus
- ↑ Factorization of a 768-bit RSA modulus
- ↑ http://www.nature.com/nature/links/011220/011220-2.html
- ↑ Lance Fortnow. Computational Complexity Blog: Complexity Class of the Week: Factoring. September 13, 2002. http://weblog.fortnow.com/2002/09/complexity-class-of-week-factoring.html
References
- Donald Knuth. The Art of Computer Programming, Volume 2: Seminumerical Algorithms, Third Edition. Addison-Wesley, 1997. ISBN 0-201-89684-2. Section 4.5.4: Factoring into Primes, pp. 379–417.
- Richard Crandall and Carl Pomerance (2001). Prime Numbers: A Computational Perspective (1st edition ed.). Springer. ISBN 0-387-94777-9. Chapter 5: Exponential Factoring Algorithms, pp. 191–226. Chapter 6: Subexponential Factoring Algorithms, pp. 227–284. Section 7.4: Elliptic curve method, pp. 301–313.
External links
- A collection of links to factoring programs
- Richard P. Brent, "Recent Progress and Prospects for Integer Factorisation Algorithms", Computing and Combinatorics", 2000, pp. 3-22. download
- Manindra Agrawal, Neeraj Kayal, Nitin Saxena, "PRIMES is in P." Annals of Mathematics 160(2): 781-793 (2004). August 2005 version PDF
- [1] is a public-domain integer factorization program for Windows. It claims to handle 80-digit numbers. See also the web site for this program MIRACL
- The RSA Challenge Numbers - a factoring challenge, no longer active.
- Eric W. Weisstein, “RSA-640 Factored” MathWorld Headline News, November 8, 2005
- Qsieve, a suite of programs for integer factorization. It contains several factorization methods like Elliptic Curve Method and MPQS.
- Source code by Paolo Ardoino, Three known algorithms and C source code.
- Factorization Source Code: by Paul Herman & Ami Fischman, C++ source code for many factorization algorithms including Pollard Rho & Shor's.
- a database containing factorizations, complete and incomplete, of over 80 million numbers.
|
|||||||||||||||||||||||||||||